Some Simple Equivalent Infinitesimals
Some Simple Equivalent Infinitesimals
Some Simple Equivalent Infinitesimals
A very simple, small, thread-safe and stream-styled logger written in C++.
A B+ Tree based local database in Modern C++.

Open-source alternative to AWCC for Dell G-series servers.

Auto Objection! An Android Ace Attorney simulator. Place the phone flat on the table and knock the desktop.

Create Virtual Serial Port with socat & Python in Linux.

Automatically fetch and compile Aseprite source code with Github Actions.

Data through port *53* is not intercepted, and the authentication system can be bypassed using the DNS channel.
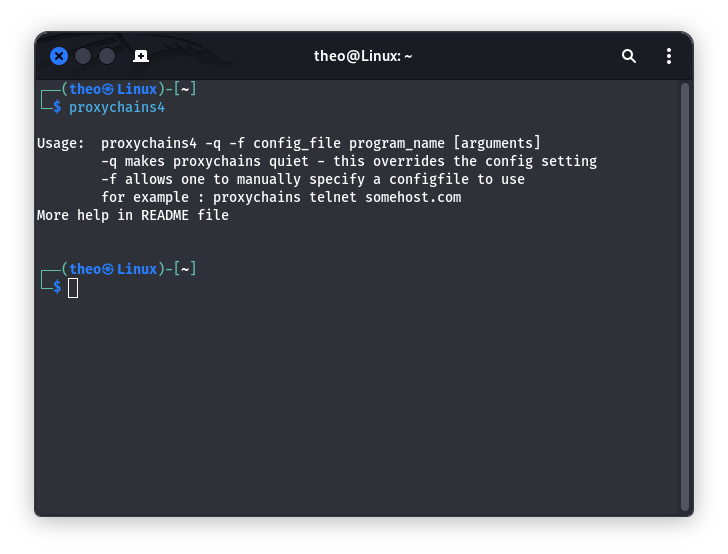
Set proxy for CMD/Powershell/Terminal/Git

mdk3 is used for **stress testing 802.11 networks(wifi)**. It consists of various methods by which we can perform tests. Some of major method sare beacon flooding, deauthentication, WPA-dos etc...